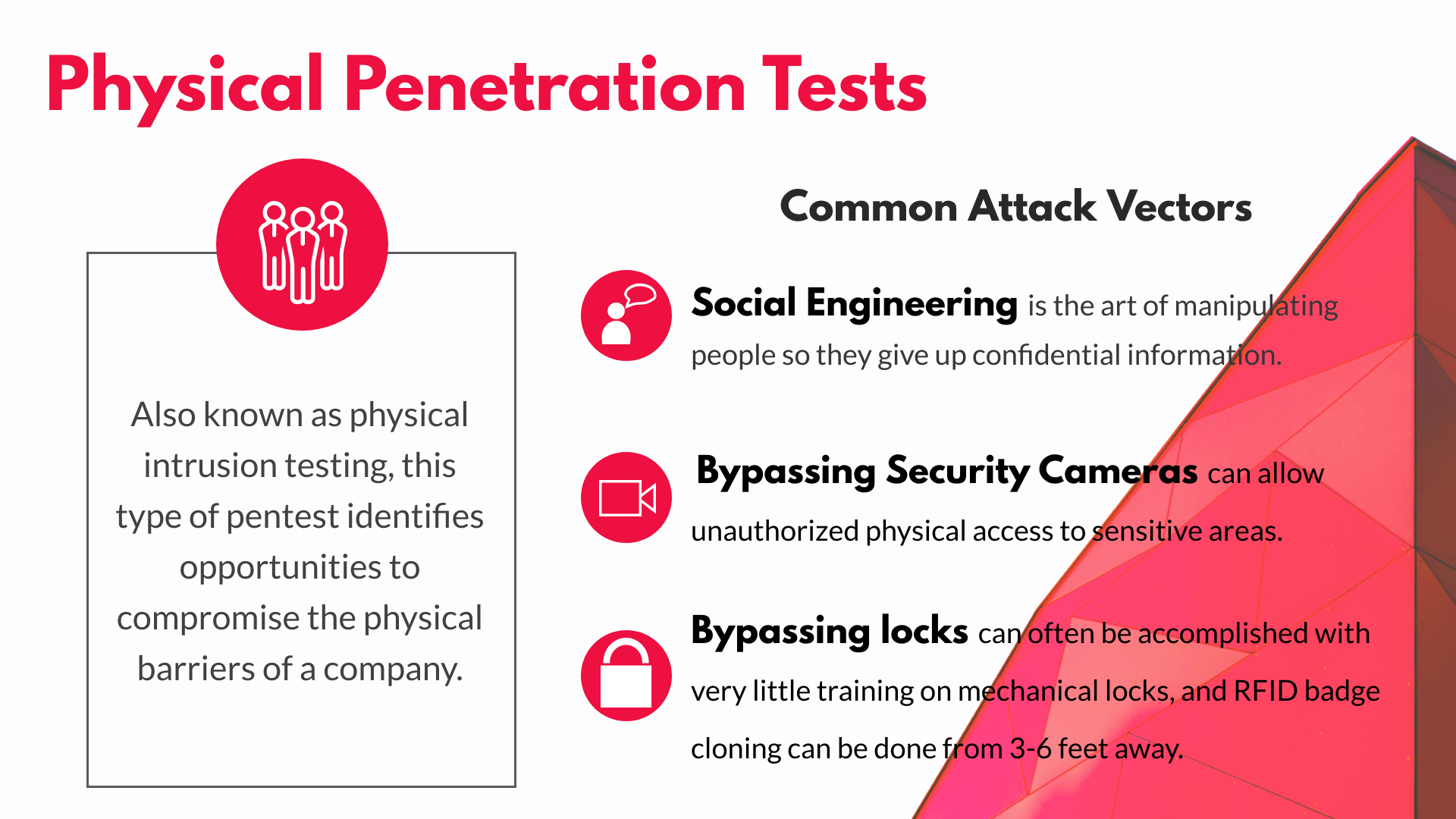
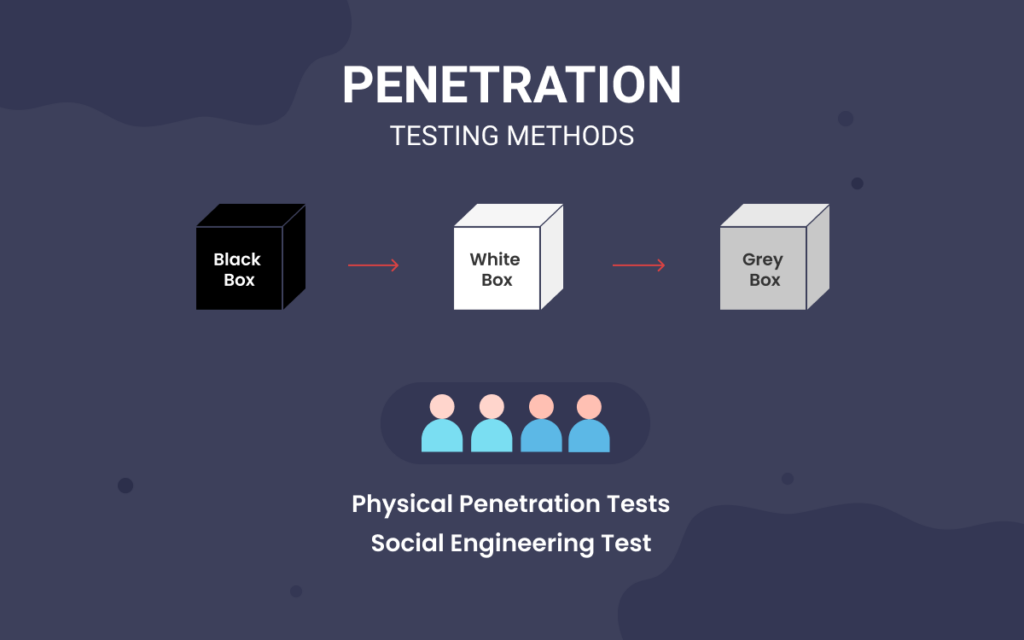
Social Engineering Penetration Testing | Managed IT Services and Cyber Security Services Company - Teceze

Social Engineering Attacks: A Look at Social Engineering Examples in Action - Hashed Out by The SSL Store™

Learn Social Engineering Pen Testing with different Module – Infosavvy Cyber Security & IT Management Trainings

Hacking for Beginners : A Step by Step Guide to Learn How to Hack Websites, Smartphones, Wireless Networks, Work with Social Engineering, Complete a Penetration Test, and Keep Your Computer Safe (Hardcover) -



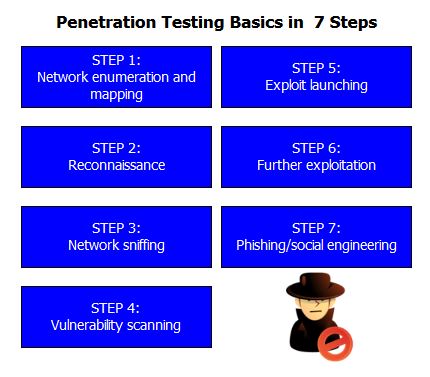
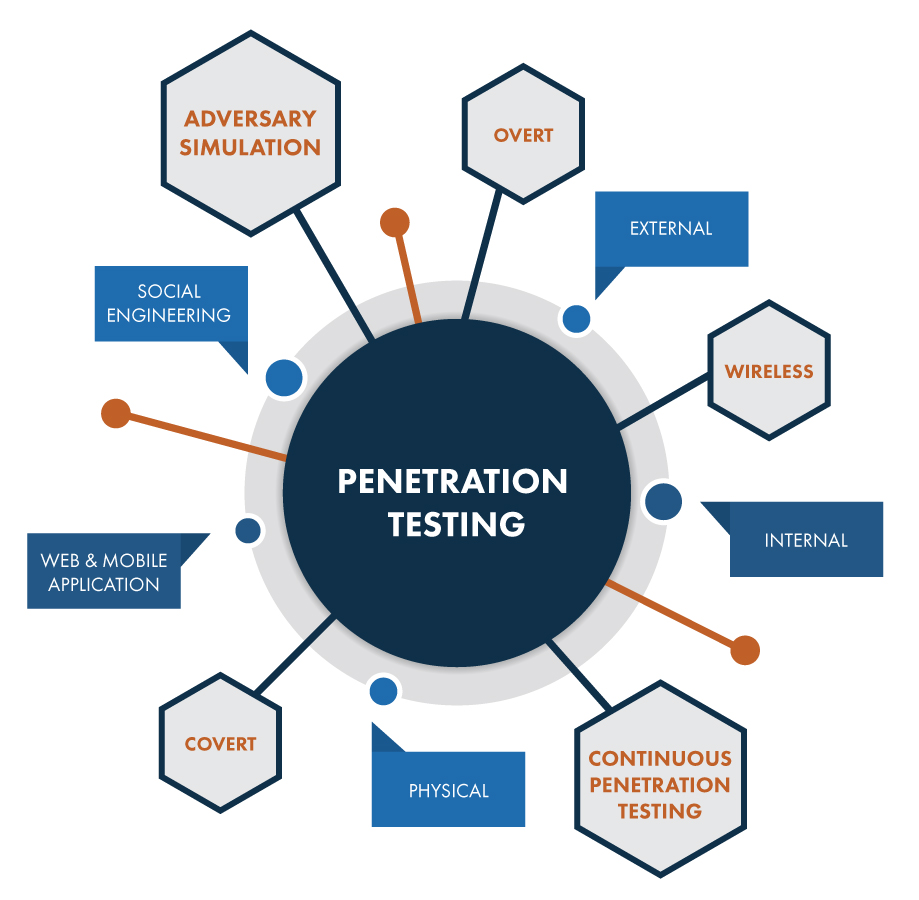


![Anatomy Of A Great Penetration Tester [Infographic] – eLearnSecurity Blog Anatomy Of A Great Penetration Tester [Infographic] – eLearnSecurity Blog](https://blog.elearnsecurity.com/wp-content/uploads/2019/02/Anatomy-Of-Penetration-Tester-Infographc-01.jpg)